* Update trivy 0.35.0->0.48.0
- Specify oras-go 1.2.4 in indirect dependencies
docker/docker changes a part of its API at 24.0
- registry: return concrete service type · moby/moby@7b3acdf
- 7b3acdff5d (diff-8325eae896b1149bf92c826d07fc29005b1b102000b766ffa5a238d791e0849bR18-R21)
oras-go 1.2.3 uses 23.0.1 and trivy transitively depends on docker/docker 24.y.z.
There is a build error between oras-go and docker/dockr.
- Update disabled analyzers
- Update language scanners, enable all of them
* move javadb init to scan.go
* Add options for java db init()
* Update scanner/base.go
* Remove unused codes
* Add some lock file names
* Typo fix
* Remove space character (0x20)
* Add java-db options for integration scan
* Minor fomartting fix
* minor fix
* conda is NOT supported by Trivy for library scan
* Configure trivy log in report command too
* Init trivy in scanner
* Use trivy's jar.go and replace client which does almost nothing
* mv jar.go
* Add sha1 hash to result and add filepath for report phase
* Undo added 'vuls scan' options
* Update oras-go to 1.2.4
* Move Java DB related config items to report side
* Add java db search in detect phase
* filter top level jar only
* Update trivy to 0.49.1
* go mod tidy
* Update to newer interface
* Refine lock file list, h/t MaineK00n
* Avoid else clauses if possible, h/t MaineK00n
* Avoid missing word for find and lang types, h/t MaineK00n
* Add missing ecosystems, h/t MaineK00n
* Add comments why to use custom jar analyzer, h/t MaineK00n
* Misc
* Misc
* Misc
* Include go-dep-parser's pares.go for modification
* Move digest field from LibraryScanner to Library
* Use inner jars sha1 for each
* Add Seek to file head before handling zip file entry
* Leave Digest feild empty for entries from pom.xml
* Don't import python/pkg (don't look into package.json)
* Make privete where private is sufficient
* Remove duplicate after Java DB lookup
* misc
* go mod tidy
* Comment out ruby/gemspec
* misc
* Comment out python/packaging
* misc
* Use custom jar
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/jar.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update detector/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update models/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/base.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/parse.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Missing changes in name change
* Update models/github.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update models/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update models/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update models/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/base.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/base.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update scanner/trivy/jar/jar.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Don't import fanal/types at github.go
* Rewrite code around java db initialization
* Add comment
* refactor
* Close java db client
* rename
* Let LibraryScanner have java db client
* Update detector/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update detector/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update detector/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* Update detector/library.go
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
* inline variable
* misc
* Fix typo
---------
Co-authored-by: MaineK00n <mainek00n.1229@gmail.com>
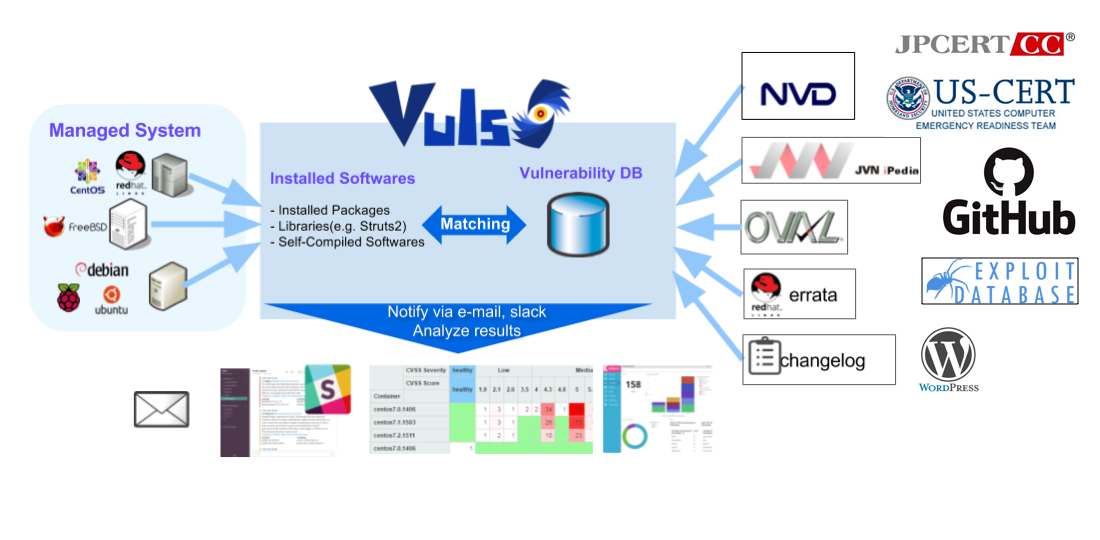
Vuls: VULnerability Scanner
Vulnerability scanner for Linux/FreeBSD, agent-less, written in Go.
We have a slack team. Join slack team
Twitter: @vuls_en
Abstract
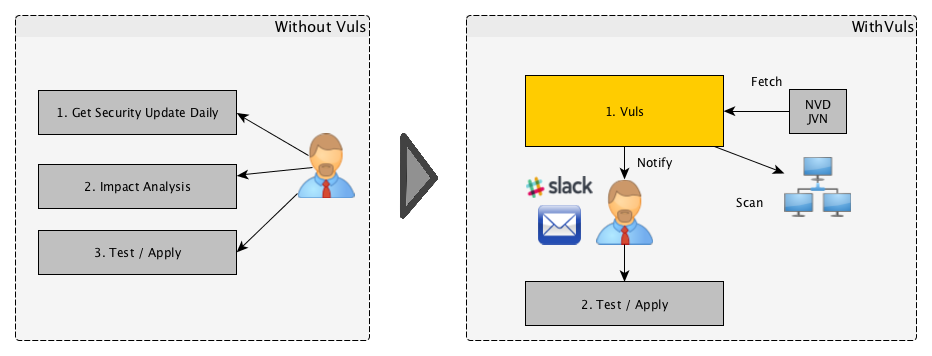
For a system administrator, having to perform security vulnerability analysis and software update on a daily basis can be a burden. To avoid downtime in a production environment, it is common for a system administrator to choose not to use the automatic update option provided by the package manager and to perform update manually. This leads to the following problems.
- The system administrator will have to constantly watch out for any new vulnerabilities in NVD (National Vulnerability Database) or similar databases.
- It might be impossible for the system administrator to monitor all the software if there are a large number of software packages installed in the server.
- It is expensive to perform analysis to determine the servers affected by new vulnerabilities. The possibility of overlooking a server or two during analysis is there.
Vuls is a tool created to solve the problems listed above. It has the following characteristics.
- Informs users of the vulnerabilities that are related to the system.
- Informs users of the servers that are affected.
- Vulnerability detection is done automatically to prevent any oversight.
- A report is generated on a regular basis using CRON or other methods. to manage vulnerability.
Main Features
Scan for any vulnerabilities in Linux/FreeBSD/Windows/macOS
Supports major Linux/FreeBSD/Windows/macOS
- Alpine, Amazon Linux, CentOS, AlmaLinux, Rocky Linux, Debian, Oracle Linux, Raspbian, RHEL, openSUSE, openSUSE Leap, SUSE Enterprise Linux, Fedora, and Ubuntu
- FreeBSD
- Windows
- macOS
- Cloud, on-premise, Running Docker Container
High-quality scan
-
Vulnerability Database
-
OVAL
-
Security Advisory
-
Commands(yum, zypper, pkg-audit)
- RHSA / ALAS / ELSA / FreeBSD-SA
- Changelog
-
PoC, Exploit
-
CERT
-
CISA(Cybersecurity & Infrastructure Security Agency)
-
Cyber Threat Intelligence(MITRE ATT&CK and CAPEC)
-
Libraries
-
WordPress
Scan mode
- Scan without root privilege, no dependencies
- Almost no load on the scan target server
- Offline mode scan with no internet access. (CentOS, Alma Linux, Rocky Linux, Debian, Oracle Linux, Red Hat, Fedora, and Ubuntu)
- Scan with root privilege
- Almost no load on the scan target server
- Detect processes affected by update using yum-ps (Amazon Linux, CentOS, Alma Linux, Rocky Linux, Oracle Linux, Fedora, and RedHat)
- Detect processes which updated before but not restarting yet using checkrestart of debian-goodies (Debian and Ubuntu)
- Offline mode scan with no internet access. (CentOS, Alma Linux, Rocky Linux, Debian, Oracle Linux, Red Hat, Fedora, and Ubuntu)
Remote, Local scan mode, Server mode
- User is required to only set up one machine that is connected to other target servers via SSH
- If you don't want the central Vuls server to connect to each server by SSH, you can use Vuls in the Local Scan mode.
- First, start Vuls in server mode and listen as an HTTP server.
- Next, issue a command on the scan target server to collect software information. Then send the result to Vuls Server via HTTP. You receive the scan results as JSON format.
- No SSH needed, No Scanner needed. Only issuing Linux commands directory on the scan target server.
Dynamic Analysis
- It is possible to acquire the state of the server by connecting via SSH and executing the command.
- Vuls warns when the scan target server was updated the kernel etc. but not restarting it.
Scan vulnerabilities of non-OS-packages
- Libraries of programming language
- Self-compiled software
- Network Devices
Vuls has some options to detect the vulnerabilities
- Lockfile based Scan
- GitHub Integration
- Common Platform Enumeration (CPE) based Scan
- OWASP Dependency Check Integration
Scan WordPress core, themes, plugins
MISC
- Nondestructive testing
- Pre-authorization is NOT necessary before scanning on AWS
- Vuls works well with Continuous Integration since tests can be run every day. This allows you to find vulnerabilities very quickly.
- Auto-generation of configuration file template
- Auto-detection of servers set using CIDR, generate configuration file template
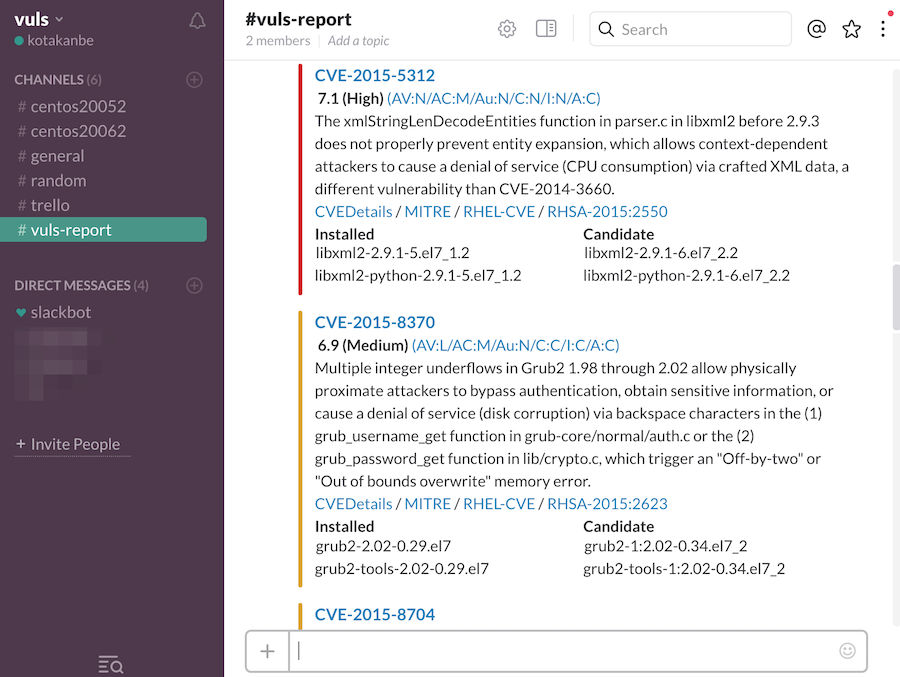
- Email and Slack notification is possible (supports Japanese language)
- Scan result is viewable on accessory software, TUI Viewer in a terminal or Web UI (VulsRepo).
What Vuls Doesn't Do
- Vuls doesn't update the vulnerable packages.
Document
For more information such as Installation, Tutorial, Usage, visit vuls.io
日本語翻訳ドキュメント
Authors
kotakanbe (@kotakanbe) created vuls and these fine people have contributed.
Contribute
see vulsdoc
Sponsors
License
Please see LICENSE.